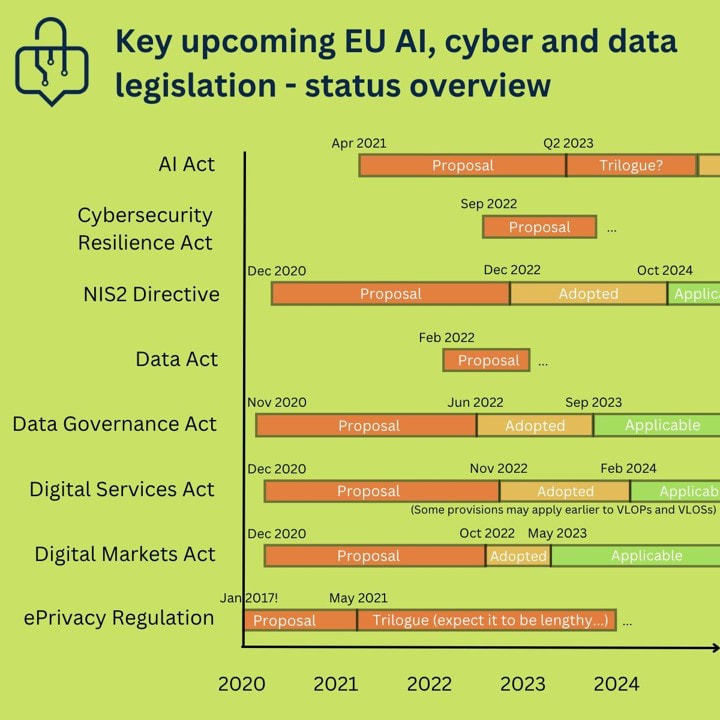
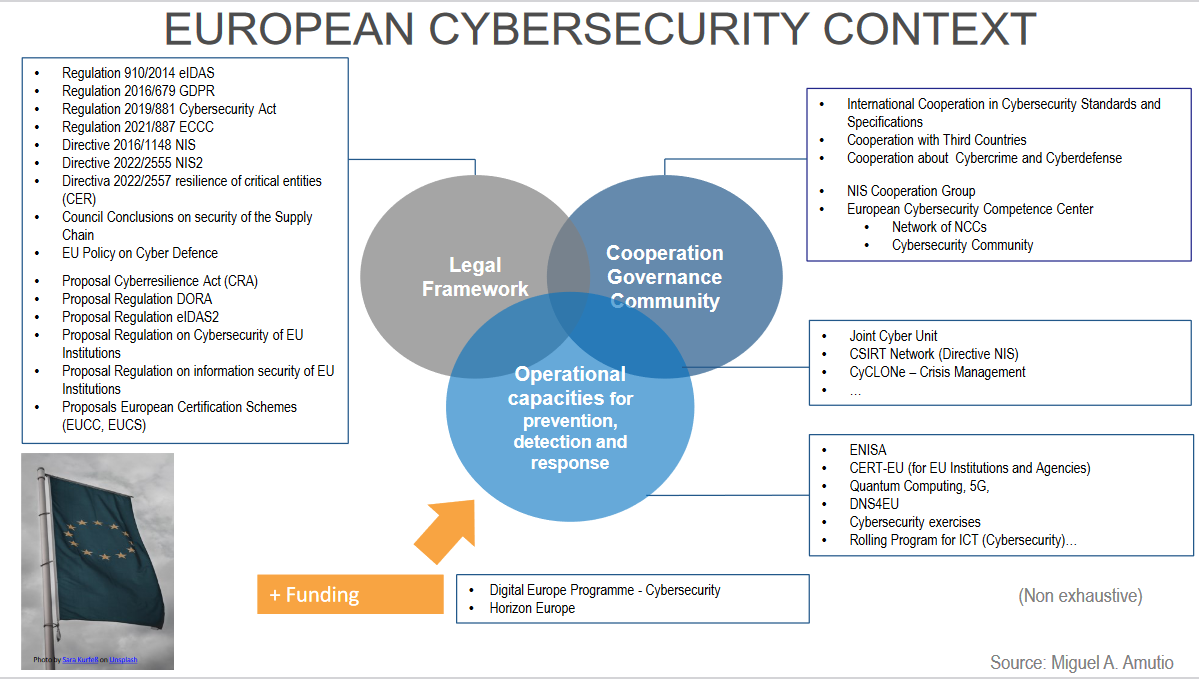
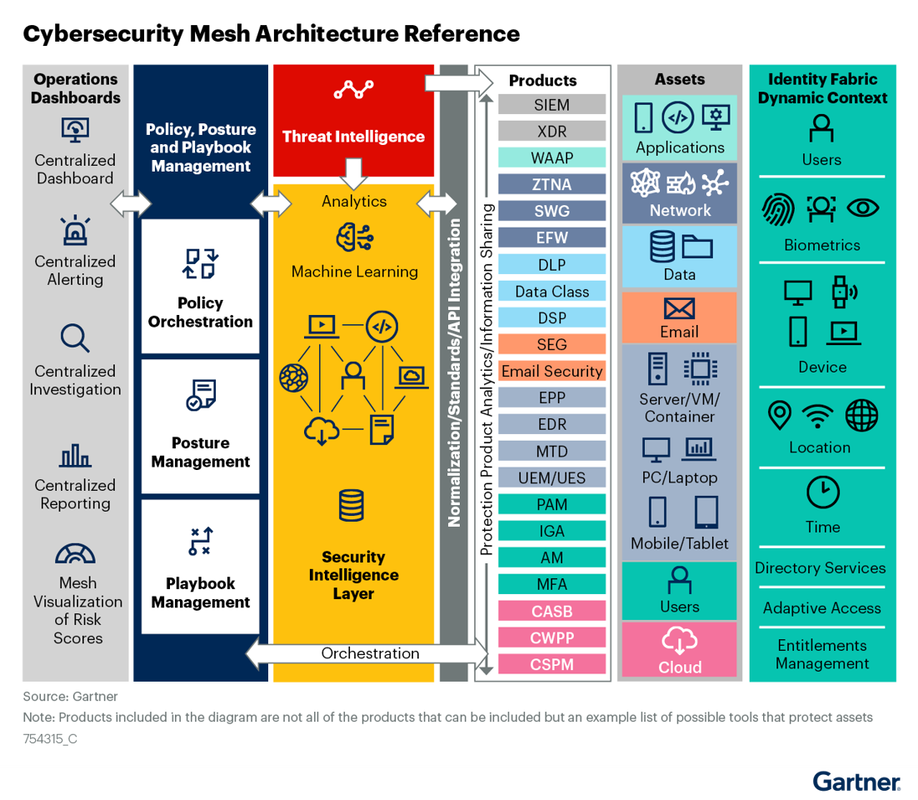
Key upcoming eu ai, cyber and data legislation
|
AI ACT: https://en.wikipedia.org/wiki/Artificial_Intelligence_Act
Cybersecurity Resilience Act: https://digital-strategy.ec.europa.eu/en/library/cyber-resilience-act NIS2 Network & Information Systems 2: https://www.europarl.europa.eu/thinktank/en/document/EPRS_BRI(2021)689333 Data Act: https://digital-strategy.ec.europa.eu/en/library/data-act-proposal-regulation-harmonised-rules-fair-access-and-use-data Data Governance Act: https://en.wikipedia.org/wiki/Data_Governance_Act Digital Service Act: https://en.wikipedia.org/wiki/Digital_Services_Act Digital Markets Act: https://en.wikipedia.org/wiki/Digital_Markets_Act ePrivacy Regulation: https://digital-strategy.ec.europa.eu/en/policies/eprivacy-regulation Source: AI4Belgium’ Whatsapp group |
European cybersecurity context
cybersecurity mesh architecture reference by gartner
CISSP - 8 Domains
- Security and Risk Management
- Asset Security
- Security Architecture and Engineering
- Communication and Network Security
- Identity and Access Management (IAM)
- Security Assessment and Testing
- Security Operations
- Software Development Security
https://www.isc2.org/Certifications/cissp/Certification-Exam-Outline
Security and Risk Management – CIA Triad, IAAAA, Risk management, Threat identification, DRP/BCP, Types of Law, IP
Asset Security – Classification level, Data retention durations - Security controls - Ownership – Classification criteria, Retention policies – Remanence (données qui persistent malgré l’effacement), Standards
Security Architecture and Engineering – Models, Concepts, Evaluation and Assurance Levels, Hardware Architecture, Virtualization, Memory protection, Cryptography, Web security, Codes vs. Ciphers, Symm. Asymm. Encryption, Mobile Security, IoT, Physical security, Site selection, Fire extinguishers
Communication and Network Security – OSI Reference Model, TCP 3-way handshake, (A)DSL, LAN Packet transmission, TCP Protocols, Attacks on OSI layers, Hardware devices, Firewall and Perimeter security, Leased Lines, Network attacks, IP Addresses, Network types, Networking Methods and Standards, Email security, Port ranges, Remote Access Services, VPN Encryption, Communication Hardware Devices, WAN Transmission types, Wireless networking, Firewall Generation Evolution
Identity and Access Management (IAM) – 3FA (knowledge, ownership, characteristic), Terminology, Level of Access & Control, SSO, Access stances (allow deny by default), Authorization, Auth. Methods, Auth. Methods/Concepts, Access Control Types, User Account management, Access Control Mgt, SESAME, Auth. Concepts, Federal models, Access Control Models, Access Control categories, Vulnerability assessment, password types
Security Assessment and Testing – Software testing, Log mgt system, Threat assessment modeling, Software development security best practices, security testing
Security Operations – Incident scene, Live evidence, Asset management, IDS & IPS, Firewall, Hierarchical Recovery types, Types of system failure, Data destruction and Reuse, DRP, Characteristics of Evidence, Interviewing and Interrogation, Network analysis, Governing laws, DLP, Digital Data States, Backup types, Disaster Recovery Test, BCP development, Evidence Lifecycle, Digital evidence, Media analysis, Admissible evidence, Digital forensics, Investigation to determine suspect, SIEM, Transaction Redundancy Implementations, System hardening (reinforcement), System recovery, Configuration management, Incident response, Root Cause Analysis, Disaster Recovery Methods, RAID – SAN - & NAS, Trusted Recovery
Software Development Security – SDLC, DevOps, Software Development Methods, Programming Language Types, Database Architecture and Models, Database Interface Languages, Knowledge management, Covert Channels (storage & timing), Security assessment & Testing terms, Data warehouse and Data mining, Database threats, ACID, Traditional SDLC, Object-Oriented technology terminology, Trusted Computer Base, change management process, Configuration management process, Capability Maturity Model, Project management tools, Phase of Object-Oriented design, Virus types, anti-virus types, protection rings
Source:
https://www.comparitech.com/blog/information-security/cissp-certification-courses/
https://www.isc2.org/Certifications/cissp/Certification-Exam-Outline
Asset Security – Classification level, Data retention durations - Security controls - Ownership – Classification criteria, Retention policies – Remanence (données qui persistent malgré l’effacement), Standards
Security Architecture and Engineering – Models, Concepts, Evaluation and Assurance Levels, Hardware Architecture, Virtualization, Memory protection, Cryptography, Web security, Codes vs. Ciphers, Symm. Asymm. Encryption, Mobile Security, IoT, Physical security, Site selection, Fire extinguishers
Communication and Network Security – OSI Reference Model, TCP 3-way handshake, (A)DSL, LAN Packet transmission, TCP Protocols, Attacks on OSI layers, Hardware devices, Firewall and Perimeter security, Leased Lines, Network attacks, IP Addresses, Network types, Networking Methods and Standards, Email security, Port ranges, Remote Access Services, VPN Encryption, Communication Hardware Devices, WAN Transmission types, Wireless networking, Firewall Generation Evolution
Identity and Access Management (IAM) – 3FA (knowledge, ownership, characteristic), Terminology, Level of Access & Control, SSO, Access stances (allow deny by default), Authorization, Auth. Methods, Auth. Methods/Concepts, Access Control Types, User Account management, Access Control Mgt, SESAME, Auth. Concepts, Federal models, Access Control Models, Access Control categories, Vulnerability assessment, password types
Security Assessment and Testing – Software testing, Log mgt system, Threat assessment modeling, Software development security best practices, security testing
Security Operations – Incident scene, Live evidence, Asset management, IDS & IPS, Firewall, Hierarchical Recovery types, Types of system failure, Data destruction and Reuse, DRP, Characteristics of Evidence, Interviewing and Interrogation, Network analysis, Governing laws, DLP, Digital Data States, Backup types, Disaster Recovery Test, BCP development, Evidence Lifecycle, Digital evidence, Media analysis, Admissible evidence, Digital forensics, Investigation to determine suspect, SIEM, Transaction Redundancy Implementations, System hardening (reinforcement), System recovery, Configuration management, Incident response, Root Cause Analysis, Disaster Recovery Methods, RAID – SAN - & NAS, Trusted Recovery
Software Development Security – SDLC, DevOps, Software Development Methods, Programming Language Types, Database Architecture and Models, Database Interface Languages, Knowledge management, Covert Channels (storage & timing), Security assessment & Testing terms, Data warehouse and Data mining, Database threats, ACID, Traditional SDLC, Object-Oriented technology terminology, Trusted Computer Base, change management process, Configuration management process, Capability Maturity Model, Project management tools, Phase of Object-Oriented design, Virus types, anti-virus types, protection rings
Source:
https://www.comparitech.com/blog/information-security/cissp-certification-courses/
https://www.isc2.org/Certifications/cissp/Certification-Exam-Outline
Cybersecurity projects
|
Security and Risk management
CIAA IAAAA Risk management Asset security Data Loss Prevention - O365 Security Architecture and Engineering Managed Workplace Management Azure Hybrid Cloud Security MDM Mobile Device Management (Usage de MSFT Intune) MDM Creation du document juridique Communication and Network Security Network Segmentation VPN par défaut Outil de gestion des DNS Décommissionnement du réseau Identity and Access Management (IAM) Multi-factor authentication Mise en place de l’Identity and Access Management |
Security Assessment and Testing
ARA Architecture Risks Analysis Cartographie des flux des données Penetration testing Access Review (personnel, externes) Access Control Security Operations Data anonymization SIEM SOC Mise en place de la gouvernance de la détection Mise en place d’un runbook de réponse à un incident Certification ISO 27001 & Mise en place SMSI Campagne de sensibilisation à la sécurité ISMS – Référentiel de sécurité de l’information Software Development Security SSDLC Secured Software Development Lifecycle Sécurisation de containers de type Docker Anti-virus pour fichiers uploadés sur nos Apps |